
WWPass Key Set https://www.wwpass.com/wwpass-key-set
The WWPass Key Set represents a practical approach to modern authentication challenges, combining hardware-backed credentials, privacy-aware design, and centralized lifecycle management. As organizations face increasingly sophisticated threats and evolving regulatory requirements, the need for authentication mechanisms that do not rely on static passwords or vulnerable shared secrets becomes critical. The WWPass Key Set offers a turnkey option for enterprises seeking to deploy strong multi-factor authentication with minimal friction for users and administrators alike.
At its core, the WWPass Key Set bundles secure cryptographic tokens and management tools that together create a complete credential ecosystem. Each key is designed to store private cryptographic material inside tamper-resistant hardware, preventing extraction even if the device is lost or stolen. Authentication is performed using standard public-key mechanisms, where the server verifies a signature or a challenge response tied to the device without ever needing to store a reusable secret. This reduces attack surfaces associated with password databases and helps defend against phishing, credential theft, and replay attacks.
One of the main advantages of using a hardware-backed key set is the delineation between identity and possession. Users authenticate by proving possession of a device and, depending on policies, may combine that possession factor with a PIN or biometric check. This layered approach supports common authentication flows such as single sign-on (SSO), VPN access, remote desktop protocols, and secure access to cloud services. Because authentication relies on asymmetric cryptography, systems can be configured to permit revocation, rotation, and renewal of credentials without compromising ongoing services.
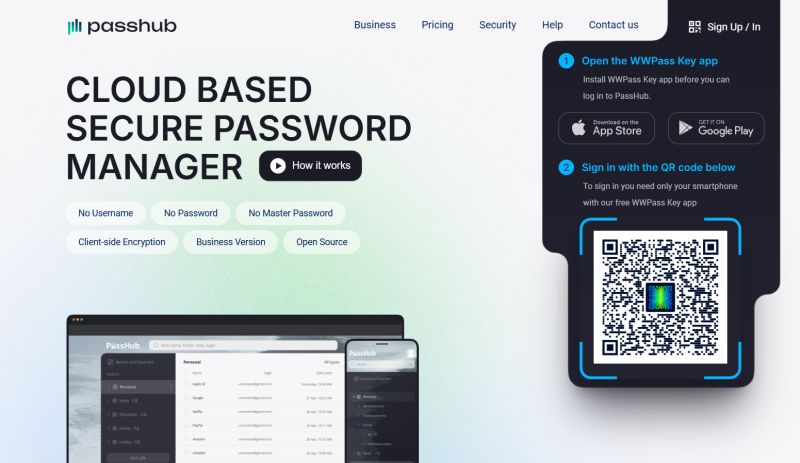
Privacy and user control are central to the WWPass model. The system is built to minimize the amount of personally identifiable information tied to the authentication process while still maintaining enterprise-grade auditability and compliance capabilities. Administrators can manage keys, assign policies, and audit usage patterns without exposing user secrets. This separation helps organizations adhere to data protection regulations and reduces the risk of large-scale data breaches arising from centralized secret stores.
Deployment of the WWPass Key Set can follow several patterns depending on organizational needs. For new deployments, companies may adopt a phased rollout: pilot a small group, integrate with identity providers and SSO systems, then expand to broader user populations. For organizations that already use identity and access management (IAM) solutions, the WWPass Key Set can complement existing ecosystems by providing a stronger second factor or an alternative to SMS- or app-based push methods. Integration options typically include standard protocols and APIs, which reduces vendor lock-in and eases adoption with minimal changes to application code.
Management is designed to be enterprise-friendly. The WWPass Key Set includes tools for provisioning, inventory, and lifecycle actions such as key replacement or revocation. Administrators can set policies that enforce PIN complexity, require periodic revalidation, or restrict allowed authentication contexts (for example, limiting access from certain geographic locations or devices). Automated workflows for lost or stolen keys allow rapid suspension and reissue, lowering the operational cost of incidents while maintaining continuity for end users.
From a security architecture standpoint, the WWPass Key Set supports features that are important in high-assurance environments. Keys are generated and stored on-device, preventing duplication. Authentication events can be cryptographically bound to session parameters, making man-in-the-middle or replay attacks ineffective. In addition, the system supports mutual authentication, enabling both client and server to assert authenticity in sensitive interactions. Strong auditing and tamper-evident logs help security teams investigate incidents and satisfy audit requirements.
One practical concern organizations often have is usability. Strong security measures must balance protection with user experience to ensure adoption. The WWPass Key Set is designed with that balance in mind: credential use is straightforward for end users, typically requiring only a single step such as touching a token or entering a short PIN. Because the token handles heavy cryptographic operations, authentication is fast and consistent across devices and network conditions. Training and onboarding can be streamlined through clear documentation and managed provisioning processes.

Another benefit of hardware-backed keys is the ability to implement granular access controls. Enterprises can create role-based policies that map authentication strength and key attributes to resource access levels. For example, high-risk operations or administrative interfaces can be restricted to users with keys that meet stricter hardware or enrollment criteria. Such an approach supports least-privilege principles and reduces the potential impact of compromised accounts.
Cost and total cost of ownership (TCO) are important considerations. While hardware tokens incur an upfront expense, they can reduce long-term costs associated with password resets, account takeovers, and fraud. The WWPass Key Set aims to provide a predictable economic model by offering bundled solutions that include tokens and management features. When calculating ROI, organizations should consider reduced support overhead, improved compliance posture, and lower incidence of security breaches as part of the overall value proposition.
Security teams evaluating the WWPass Key Set should consider threat models specific to their environment. While hardware-backed keys mitigate many common threats, they should be used in conjunction with solid endpoint hygiene, network defenses, and monitoring. Additional protections such as device attestation, encrypted communication channels, and anomaly detection can strengthen the overall posture. It is also important to plan for lifecycle events such as loss, damage, or employee offboarding to ensure keys are revoked promptly.
Compliance-minded organizations will appreciate features that support regulatory frameworks. The WWPass Key Set can assist in meeting requirements for multi-factor authentication (MFA), strong cryptographic controls, and audit trails. Integration with identity governance and administration (IGA) systems can help enforce access policies and document compliance efforts. For regulated industries such as finance, healthcare, and government, hardware-backed authentication provides a strong signal during audits and risk assessments.
In conclusion, the WWPass Key Set provides organizations with a robust, privacy-conscious, and manageable approach to strong authentication. By combining hardware security, straightforward user experience, and centralized management, it addresses both technical and operational challenges of modern access control. For enterprises evaluating options to replace or augment password-based systems, the WWPass Key Set offers a compelling mix of security, usability, and administrative control that can be tailored to diverse deployment scenarios and compliance requirements.
